Monitoring DMARC with Docker
... and a bit of ansible. If you are a regular reader of this blog, firstly thanks it means a lot and secondly, you'll know I've been doing a lot of stuff with Ansible automating docker image deployments. To add to this, I though I would look in to how to automate docker compose files, and get around to actually looking at my DMARC data.
To start off with, you are going to need a domain name and DMARC set up. If you have never set it up before, you could just set up a DMARC record with a policy of none, or you could follow this post I did some time ago and get everything fully working.
The other pre-requisite is the place to host the container.
Setting up docker compose in docker was quite straight forward. I would have liked to have been able to set the volume name dynamically, but that escaped me at the moment.
---
- name: "DMARC Reporter"
hosts: docker.host
become: yes
become_method: sudo
vars:
- container: dmarc-report
- dbcontainer: mariadb
- dbusername: 'dmarc_report'
- dbpassword: 'normalpass'
- dbrootpass: 'dbrootpass'
tasks:
- name: Start dmarc-reporter project with inline definition
community.docker.docker_compose:
project_name: dmarc-reporter
definition:
version: '2'
volumes:
mariadb-database:
services:
db:
image: mariadb:10
command: --skip-innodb-read-only-compressed
environment:
- "MYSQL_ROOT_PASSWORD={{ dbrootpass }}"
- "MYSQL_DATABASE=dmarc_report"
- "MYSQL_USER={{ dbusername }}"
- "MYSQL_PASSWORD={{ dbpassword }}"
volumes:
- "mariadb-database:/var/lib/mysql"
healthcheck:
test: ["CMD", "mysqladmin", "ping", "-h", "localhost", "-uroot", "-p{{ dbrootpass }}"]
interval: 10s
timeout: 10s
retries: 5
dmarc-report:
image: "gutmensch/dmarc-report:latest"
hostname: dmarc-report
container_name: "{{ container }}"
ports:
- "80:80"
environment:
- "REPORT_DB_HOST=db"
- "REPORT_DB_PORT=3306"
- "REPORT_DB_NAME=dmarc_report"
- "REPORT_DB_USER={{ dbusername }}"
- "REPORT_DB_PASS={{ dbpassword }}"
- "PARSER_IMAP_SERVER=mail.host"
- "PARSER_IMAP_PORT=143"
- "PARSER_IMAP_USER=user@mail.host"
- "PARSER_IMAP_PASS=emailpassword"
- "PARSER_IMAP_READ_FOLDER=INBOX"
- "PARSER_IMAP_MOVE_FOLDER=dmarc_processed"
- "PARSER_IMAP_MOVE_FOLDER_ERR=dmarc_error"
depends_on:
- db
register: output
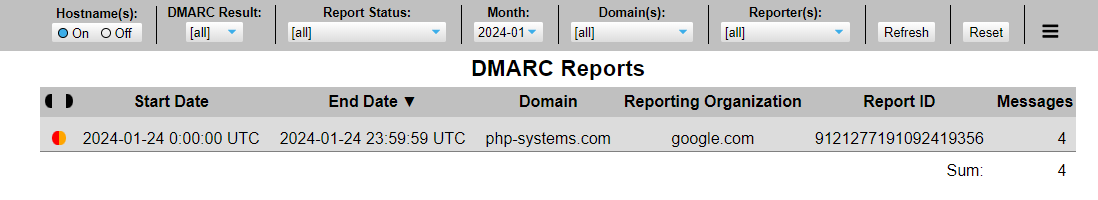
I deployed this container to my docker host, setting the environments up correctly to login in to my email and process the reports. Once completed, I pointed my web browser at my docker host, and was greated by the following:
Clicking on the line gave me some more detail
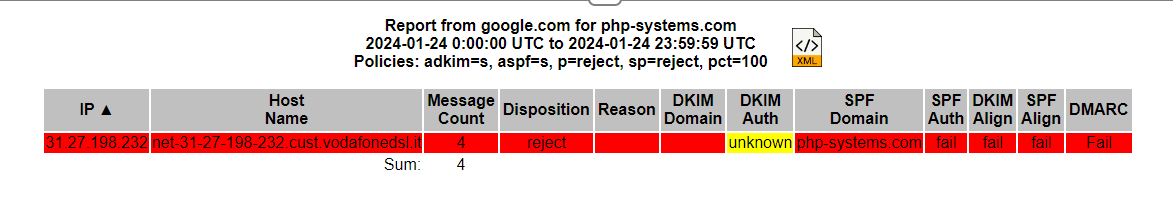
The report you can see is an actual spammer trying to pretend to be me. My domain isn't exactly massive or a big target, and yet I have spammers trying to use it. Image what people are trying to do with yours...
About the author
Tim Wilkes is a UK-based security architect with over 15 years of experience in electronics, Linux, and Unix systems administration. Since 2021, he's been designing secure systems for a telecom company while indulging his passions for programming, automation, and 3D printing. Tim shares his projects, tinkering adventures, and tech insights here - partly as a personal log, and partly in the hopes that others will find them useful.
Want to connect or follow along?
LinkedIn: [phpsytems]
Twitter / X: [@timmehwimmy]
Mastodon: [@timmehwimmy@infosec.exchange]
If you've found a post helpful, consider supporting the blog - it's a part-time passion that your support helps keep alive.
⚠️ Disclaimer
This post may contain affiliate links. If you choose to purchase through them, I may earn a small commission at no extra cost to you. I only recommend items and services I’ve personally read or used and found valuable.
As an Amazon Associate I earn from qualifying purchases.